ISE's Evil Default
Whilst working with Cisco ISE recently, I became aware of a setting within the product that could be a major ‘gotcha’ if you aren’t aware of it. We’ll take a very quick look at it in this article.
Background
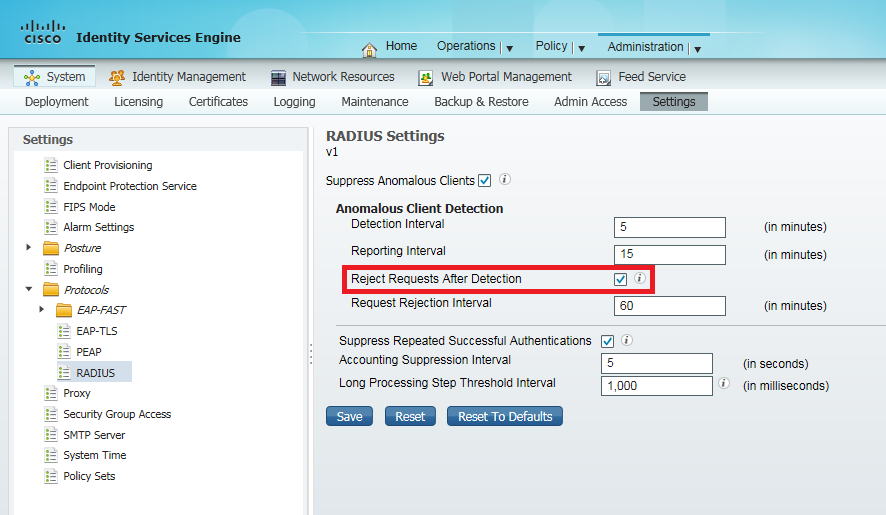
Tucked away in the depths of the Cisco ISE menu structure is a rather innocent-looking configuration setting under the ‘Anomalous Client Detection’ section of the System Settings. The option I’m referring to can be found in the following location in ISE 1.2:
Administration > System> Settings > Protocols > RADIUS
The screenshot below shows the settings page I am discussing:
The settings on this page have been provided to protect ISE in the face of an onslaught of misbehaving or mis-configured clients that may flood it with authentication traffic (and hence RADIUS traffic). In larger environments, this could become an issue and affect ISE’s performance.
Suppress Anomalous Clients
The tick-box ‘Suppress Anomalous Clients’ provides a very useful function by quieting down the ‘noise’’ that you will start to see in the ISE logs once a reasonable number of clients are using the network. Instead of providing a line of information for each client transaction in the clients logs, only the most recent successful event is shown, providing a more manageable list of transactions to view. This effect is provided by the ‘Suppress Repeated Successful Authentications’ check-box, which is checked by default.
Reject Requests After Detection
One default side-effect of selecting the suppression of anomalous clients is that by default, the ‘Reject Requests After Detection’ check-box is also checked (highlighted in the graphic above). This is the ‘evil default’.
One might expect this option to simply provide another level of event suppression for misbehaving clients. Unfortunately, having this check-box enabled will actually add clients to an internal black-list of misbehaving clients for the period specified in the ‘Request Reject Interval’ - 60 minutes by default. Clients on this black-list will be ignored by ISE and effectively excluded.
Unfortunately, from the information I have been able to uncover so far, the internal black-list of excluded clients is not available to view, so there is no obvious way of knowing which clients have fallen foul of rejection (and hence exclusion) for being an ‘anomalous client’.
Exactly what qualifies a client as being anomalous isn’t too clear - the ‘Detection Interval’ and ‘Reporting Interval’ provide some clues, but they still don’t provide any clues about how many times a client has to be ‘anomalous’ to trip the rejection criteria.
Failure Scenario
Although the feature discussed above may not seem particularly worrisome, there are situations when it can kick-in and potentially take down your whole network for an hour (using the defaults).
If there is an extended period of time where clients are failing authentication, then if the anomalous client settings are enabled and left at default, all clients may become effectively excluded for an hour. A scenario such as the failure of an external authentication source (e.g. AD) or a policy configuration error could create such a situation. And, yes, I am speaking from experience of falling foul of such a scenario.
I’m not sure of Cisco’s official recommendation for this particular area of configuration, but I would think it is at least worth winding down the default ‘Request Rejection Interval’ to a lower value than 60 minutes - that’s a long time to lose your clients.
References
Cisco ISE 1.2 User Guide: http://www.cisco.com/c/en/us/td/docs/security/ise/1-2/user_guide/ise_user_guide/ise_ui_reference_administration.html#pgfId-1293445